Onevinn PKI based DKE
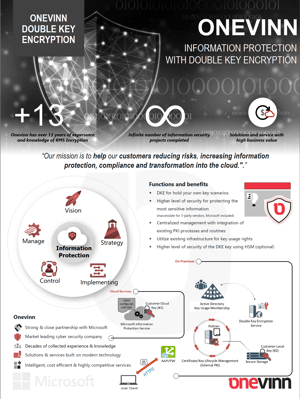
Double Key Encryption effectively replaces Microsoft Azure Hold your Own Key (HYOK), applying two layers of security to the most sensitive content in the Azure cloud. This also reduces the infrastructure footprint needed as the presence of Active Directory and Rights Management Servers are not required. Instead, one can utilize its own cryptographic keys, which in turn can be protected with existing (secure) key hosting and storage. Based on the integration with existing Public Key Infrastructure (PKI), one continues to keep control of the key, which is governed by existing policies with the additional control of the software that manages it. This integrated solution contributes to give the following functions and benefits:
Functions:
• MS DKE Web for hold your own key scenarios with support for HSM integration
• Extra layer of encryption in your Information Protection solution
• Integration with internal PKI
• Utilize existing infrastructure for key usage rights
Benefits:
• Higher level of security for end user protecting most sensitive company information/documents
• Higher level of security of the DKE key using HSM (optional)
• Centralized management of key in internal PKI
MIP is a solution that enables native/built-in labeling and encryption of documents in Windows without having to bother users with the generation of encryption keys (this is solved by Microsoft).
In some cases an organization wants to hold their own encryption keys (HYOK) and this is where DKE Web comes in.
This is a service that is hosted in your organization and your organization have full control of these keys, meaning that not even Microsoft has a way of reading your documents.
This is done through a process called ”Double Key Encryption” (DKE).
See more here how DKE works with MIP: Double Key Encryption by Microsoft (onevinn.com)